Set badge security properties that correspond to the type of authentication and encryption employed by your wireless network.
If you are deploying multiple types of Vocera badges, you can configure them to reside on separate SSIDs and take advantage of the enhanced security support offered by newer badge models. If all your badges reside on the same SSID, the security you choose must be supported by all badge types. See About Badge Profiles for information about configuring badges on separate SSIDs.
For more information about the security systems supported by Vocera, see the Vocera Infrastructure Planning Guide. The rest of this section describes how to use the Badge Properties Editor to configure badge security settings.
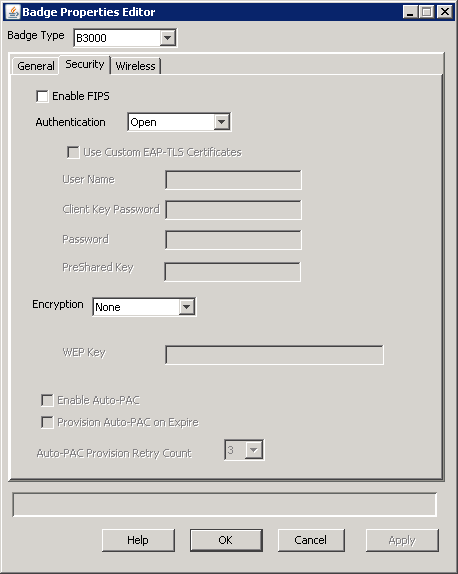
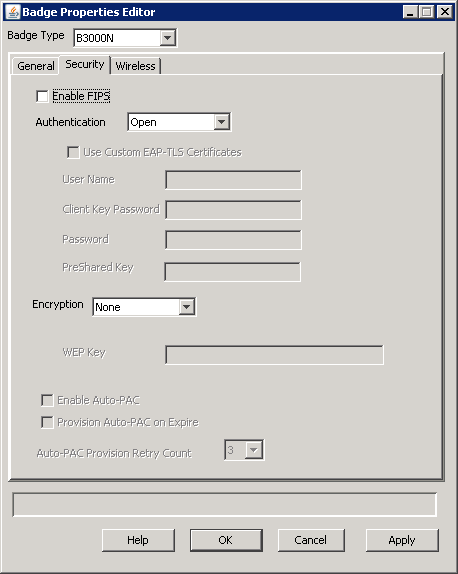
| Property | Description | Badge Types Supported |
|---|---|---|
|
Enable FIPS |
When enabled, this property causes the badge cryptographic security module to run in a secure mode that conforms with Federal Information Processing Standard (FIPS) 140-2. See About Federal Information Processing Standard (FIPS). By default, this property is not selected. This property applies only to B2000 and B3000 badges currently. When the Enable FIPS box is checked, the B3000 requires WPA2-PSK, WPA2-PEAP, or WPA2-TLS. See Enabling FIPS mode for B3000 badges for complete information on enabling these security profiles. For more information, see the Vocera Infrastructure Planning Guide. When the Enable FIPS box is checked, the B2000 requires WPA2-PSK or WPA2-PEAP. See Enabling FIPS mode for B2000 badges for complete information on enabling these security profiles. For more information, see the Vocera Infrastructure Planning Guide. |
B3000, B2000 |
| Authentication | In the Authentication field, specify whether your wireless network requires
authentication for access:
Important: If you are using EAP-FAST authentication, you can choose between automatic or manual PAC provisioning. If you choose manual PAC provisioning, you must create a .pac file on the Cisco ACS and copy it to the Vocera Voice Server and the Vocera configuration computer. See "Configuring EAP-FAST Authentication" in the Vocera Infrastructure Planning Guide. |
All |
|
Use Custom EAP-TLS Certificates |
When enabled, this property causes the badge to use custom EAP-TLS certificates rather than Vocera Manufacturer Certificates. If you use custom EAP-TLS certificates, you must generate your own self-signed certificates or obtain them from a trusted Certificate Authority (CA). If you check this box, additional configuration is required. You must install client-side certificates on the Vocera Server and the configuration computer, install the server-side certificates on your authentication server, configure your authentication server for EAP-TLS, and specify the User Name and Client Key Password properties. Alternatively, uncheck this option to use the Vocera Manufacturer Certificates. Vocera badges are preconfigured with EAP-TLS client certificates that are automatically downloaded from the Vocera Server or the Badge Configuration Unit. Vocera Manufacturer Certificates use 2048-bit RSA keys, which provide excellent security for today's enterprise and conform to industry standards and NIST recommendations. If you decide to use Vocera Manufacturer Certificates on the badge, you still need to install Vocera server-side certificates on your authentication server. By default, this property is not selected. This property is available only when the Authentication property is set to EAP-TLS. |
B3000n, B3000, B2000 |
| User Name, Password |
If your network uses either LEAP, WPA-PEAP, or EAP-FAST authentication with TKIP-WPA encryption, enter appropriate values in the User Name and Password fields. If your network uses EAP-TLS authentication with external certificates (instead of the Vocera Manufacturer Certificates), enter a value for the User Name field but not the Password field. Otherwise, skip both these fields. Each badge on a Vocera server must use the same user name and password for LEAP, WPA-PEAP, or EAP-FAST authentication. The user name format depends on requirements set by the RADIUS authentication server. For example, when using LEAP with Cisco ACS and Windows Active Directory, enter domain\userid in the User Name field, where domain is a Windows domain name and userid identifies the user. Other RADIUS servers may require the user name only. The password value is case sensitive. You can use initial or embedded spaces in either of these values; trailing spaces cause an error message when the values are saved. The badge supports a maximum of 128 alphanumeric characters for the User Name and 32 alphanumeric characters for the Password. In addition, the badge supports the following characters for LEAP passwords: ^ # ! * @ % & $ Note: If you are using EAP-FAST authentication and you change the User Name or Password values, you must also generate a new PAC file. With manual PAC provisioning, this means you must generate a new PAC file on the Cisco ACS and then copy it to the Vocera Voice Server and the Vocera configuration computer. With automatic PAC provisioning, you must restore the factory settings on the badge and then reconfigure it; see Restoring Factory Default Settings. When the badge reconnects, it retrieves the new PAC file automatically from the ACS. |
All |
| Client Key Password |
If your network uses EAP-TLS authentication and you checked the Use Custom EAP-TLS Certificates box, enter the password used to encrypt the client key. Otherwise, skip this field. The maximum length of the password is 32 alphanumeric characters. |
All |
| PreShared Key |
If your network uses WPA-PSK authentication, specify either your WPA passphrase or a 256-bit hexadecimal key hexadecimal value in the PreShared Key field. Otherwise, skip this field. If you are configuring B3000n or B3000 badges, you must specify the WPA passphrase for your wireless network. If you are configuring B2000 badges, you must specify a hexadecimal value instead of your WPA passphrase. See Entering a Pre-shared Key for WPA-PSK for additional information. |
All |
| Encryption |
In the Encryption field, choose a value from the drop-down list to specify the type of data encryption your wireless network requires. The list includes different values depending on the value in the Authentication field. If necessary, check access point settings to see which type of encryption to use. See "Master Security Table" in the Vocera Infrastructure Planning Guide for a summary of the authentication and encryption combinations supported by Vocera. |
All |
| WEP Key |
If you specified either WEP64 or WEP128 encryption, specify a value for the WEP Key field corresponding to the first WEP key slot. Use hexadecimal characters to enter the key that the access point is using. See Configuring WEP Encryption. Note: The WiFi Alliance (WFA) has deprecated support for WEP, and newer versions of wireless controllers may not have configuration options for TKIP. Even though the B3000n and B3000 badges support WEP or TKIP, Vocera recommends not using them. |
All |
| Enable Auto-PAC |
Enables automatic provisioning of the Protected Access Credential (PAC) for EAP-FAST authentication. This replaces the manual method of creating a new PAC on the Cisco ACS when it expires and then copying it to the Vocera Voice Server and the Vocera configuration computer. By default, this property is not selected. In order to take advantage of this feature, you must also select EAP-FAST authentication. Note: If you enable automatic PAC provisioning, you must increase the EAP request timeout on your access points to 15 seconds. Otherwise, automatic PAC provisioning will not work. See the Vocera Infrastructure Planning Guide for additional information. |
B3000n, B3000, B2000 |
| Provision Auto-PAC on Expire |
Enables the automatic provisioning of a new PAC when it expires. If this property is unchecked, a badge whose PAC has completely expired will display the following message: "Expired or invalid PAC credentials." Note: This message should appear only if a badge has been powered off
or did not roam at all for a while and the master key and the
retired master key on the Cisco ACS have expired. If this happens,
the badge needs to be reconfigured.
By default, this property is not selected. In order to take advantage of this feature, you must also select EAP-FAST authentication. |
B3000n, B3000, B2000 |
| Auto-PAC Provision Retry Count |
Limits the number of times a badge attempts to retry retrieving a PAC from the Cisco ACS after the first attempt failed (for example, due to wireless network problems). Select a number from 0 to 5. If a badge exceeds the retry count, it displays the following message: "Too many retries for Auto-PAC provisioning." By default, this property is set to 0 (meaning no retries). In order to take advantage of this feature, you must also select EAP-FAST authentication. |
B3000n, B3000, B2000 |